How to Keep Your Digital Life Safe and Secure
In 2018 our lives are in our pockets and in the cloud. Everything we do—from the way we communicate, to how we share photos, to how we work—often revolves around our devices. Because of the roles our smartphones and computers play in our lives, it can be easy to take things for granted and let our guards down when it comes to safety and security. Often, some of us may not realize how important it can be to keep hackers and malware out.
Luckily, iOS and macOS make it easy to stay secure; but, you need to know how to use the tools available to you—and how to recognize threats—in order to take advantage of this convenience.
If you value your safety and security, we have some information that can help you. This article aims to introduce you to the tools available on your Mac or on your iOS devices. Additionally, you'll learn about some of the ways you can recognize threats to stay safe.
20. Threats to Your Digital Life

Hackers and bots (automated software applications) are real. It's easy to dismiss something you don't see. “Out of sight, out of mind.” But although they're lurking in the shadows, they're there and remembering that can keep you safe.
But what are the shadows hackers hide in? What techniques do they use? Sometimes they hide behind a keyboard; sometimes they hide in plain sight. Understanding their methods is the best way to keep your guard up.
19. Phishing

Perhaps the most well known—and most underestimated attack—is called phishing. This is a technique used to get you to unexpectedly handover your login credentials.
To pull this off, hackers setup a website with a login page asking for your username and password. Then they send an email with a link to that site. Of course, they won't be like “hey, here’s a link, click it and give us your password.” Instead, they will make the email compelling and seem legitimate.
An example might be an email that looks like it's from Apple. It will say something like “thank you for your subscription to Spotify. Your card will be charged $99 annually starting today. Click here to manage your subscription.”
Now, I don't know about you, but if I thought I'd accidentally signed up for something that costs $99 per year, I'd probably want to cancel it. And that's the point. I'm the moment you might be tempted to click the link; after all, it looks real. But when you do one of two things will likely happen: First, you may inadvertently download a malicious program known as a virus or malware. Second, you will be redirected to their phishing site. Maybe even both.
Once at the site you are asked to log in to manage your subscriptions. When you “log in” you've successfully handed over your username and password. The site may even redirect you to the actual page, so you never notice.
18. Unsecured or Public Wi-Fi

While phishing can be a sneaky way to steal your login credentials, using a Wi-Fi network that isn't password protected, is public, or is lacking security can be worse. This is because you could be sharing the network with a hacker.
Let's start with your home Wi-Fi network. If you don't use a password or if you don't have a properly configured firewall, you're basically leaving the door open to hackers. Hackers use a technique known as “wardriving” to look for unsuspecting targets.
Wardriving is where hackers drive (or walk or bike, etcetera) up and down neighborhoods and look for wireless networks that aren't password protected. When they find one, they log in and begin their dirty work.
To understand what hackers do once on your network, let’s look at public networks (Wi-Fi or wired). When you share your network with other people, you are susceptible to attack. If your computer isn't properly secured a hacker might wreak havoc. But, more than likely they'll never need to access your computer.
The reason hackers don't need to actually get into your computer is because much of what we do happens over the Internet. Since they share the same network with you, there are tools hackers can use to hijack your data and passwords. Once you've been identified—or if you're an unlucky random target—hackers can redirect and even change the data you send and receive. In one of my university courses, we setup fake pages to fool unsuspecting users. One of the easiest ways to do this is through DNS spoofing.
DNS is like your Internet phonebook. Websites are accessed using IP addresses (i.e. Google: 172.217.0.14). But since we can't remember every IP address, we associate domains (www.Google.com) with these IP addresses. Your handy-dandy DNS server looks up these IPs for you to get you to the site. DNS spoofing occurs when a hacker alters your DNS table so when you type something like “Facebook.com” you end up at a site they created and they still your login information. Then, they redirect you to the actual site as if nothing happened.
17. ClickJacking (UI Redress)

This is a big one that a lot of people fall for. It's where a popup in your browser mimics your computer’s interface. Generally, it will say something like “virus detected” and prompt you to run a scan. When you download the “virus scanner” you've actually installed malicious software pretending to be a virus scanner.
In some cases, your computer may be held ransom by ransomware. Usually the hacker will pose as Microsoft or Apple and ask you to pay a “maintenance fee” to “fix” your computer.
16. Social Engineering

You may have noticed that many of the methods described so far involve people falling for common tricks or doing things that are inherently insecure. That's because hackers need you in many cases to essentially give them what they need. In other words, hackers are con artists.
They will try to watch you type in your passwords, create Facebook posts that get you to reveal your secret questions (more on that in a minute), dumpster dive (more on that, too), and simply talk you. You read that right, some hacker might be people you converse with. So, just be smart about what information you give out.
Speaking of information, be smart about your password hints and secret questions. “Where did you go to high school” is easy to lookup and while “what was the name of your first pet” might not be known to most people, there are ways to get you to talk. For example, we've all seen those Facebook posts that say something like “What's your Harry Potter character name?” It might say something like “when were you born” and “what's your first pet’s name” then associate a name with it. All of the sudden your post about being called “Albus Von Snowball” is really a way for a hacker to know you were born June 1972 and your cat’s name was Snowball. Think before you post.
As mentioned earlier, dumpster diving is another technique used by hackers, as well as leaving flash drives on the ground. Dumpster diving allows hackers to get information from your mail, flash drives and allow hackers access to your computer when you plug them in. Don't plug in “missing” flash drives and conceal or destroy identifying traits on your trash.
15. Tools and Methods to Keep You Safe

Just as hackers have many tools and methods to steal your data, you also have many options for keeping them at bay. We will take a look at several methods tips and tricks to keep your information safe and secure.
14. Check email addresses and URLs

Keep an eye on emails addresses and URLs. If you receive an email from “Apple,” but the expanded details say from “hackerface09@scaryhackerspace.net”—okay it won't be that obvious—you know it's not from Apple. Emails from Apple and others will use their domains (i.e. name@apple.com). Same with URLs (Web addresses) they should use the proper domain.
Additionally, remember if you are phished, change your passwords—across all accounts—immediately. Even if you have different passwords or don't use an account, you just opened up a hacker playground. Hackers will use contacts and email messages to find the data and links they need to access other accounts. Additionally, they can use your contact list to phish other people, or worse, use your account to trick friends into clicking links. Another pro tip: use distribution lists and the BCC field in your email to avoid providing hacked accounts and strangers email addresses of other people.
13. FileVault 2
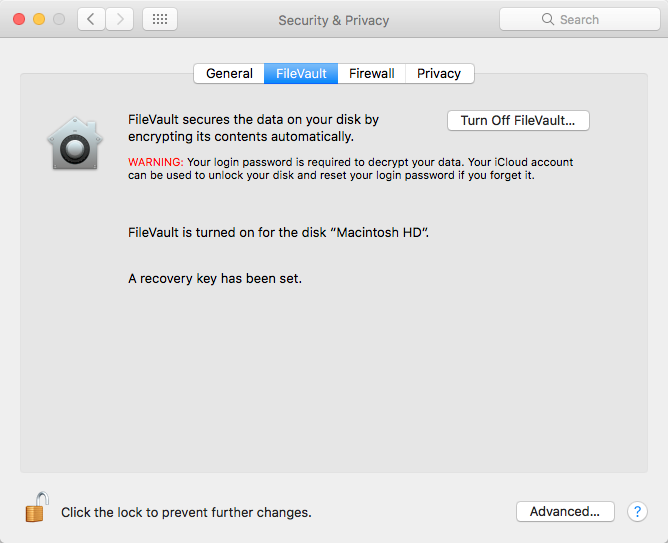
Activate FireVault on your Mac in the System Preferences under Security to encrypt your data and protect it against threats. On older Macs, you may want to install an SSD before turning on FireVault. Hard drives tend to take longer to encrypt/decrypt.
12. Find my iPhone (or Mac or iPad)

A popular hacking method is known as the “evil maid” attack. These are targeted, physical attacks on your data. To stay secure at business conferences, it's often recommended to use a “burner” computer that doesn't contain your company's secrets.
That being said, not everyone will be a target of physical attacks, but if your device is stolen you will want to be able to lock it down and possibly get it back. Find My iPhone is an iCloud feature that can help you find, lock, or erase your iOS or macOS device remotely. You may also want to consider setting up your iOS device to wipe its data after 10 failed login attempts.
11. Active screening and sandboxing

Apple’s operating systems actively screen and sandbox links and operations across many of its built-in applications (i.e. Mail, Safari, Notes, FaceTime, etcetera). Sandboxing helps keep potential malicious code separate from your data.
10. Gatekeeper
On macOS, Gatekeeper works in the background to prevent unauthorized apps from using your computer. When prompted for a username and password, read why it's needed. Make sure it's something you want to approve. If not, don't give it permission. If it continues to ask and you don't know how to make it stop, consider making a trip your nearest Apple Store for some help.
9. Privacy controls
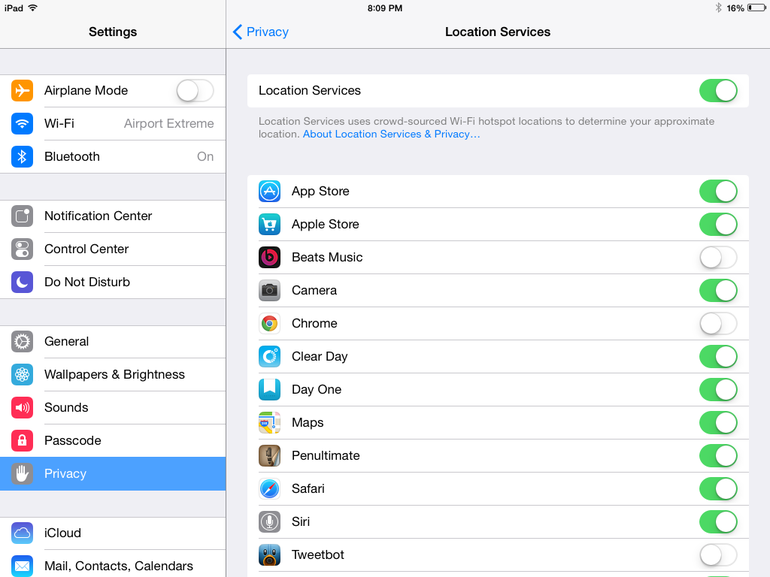
Both iOS and macOS give you control over your privacy. Your microphone, camera, location data, health data, and more are all under your control. You can even choose which apps have access to your calendar, your photos, or your smart home devices. When an app requests access to your data, think carefully—and read the description—before clicking “Allow.”
8. Safari “Safe Browsing”
Apple built Safari to be secure. It has many features built in to keep you safe while browsing the Web. It prevents tracking, it keeps advertisers off your back, and blocks pop-ups and some cookies.
7. Passwords and passcodes

True security starts with a secure password. While six-digit pins are convenient, they aren't secure. Consider a long password consisting of letters, numbers, and symbols (length is what really matters though) for your device and all your accounts.
6. Touch ID and Face ID

Of course, long, complex passwords are hard to remember and often inconvenient to type. That's where biometrics come into play. Touch ID on your macOS or iOS device lets you use your fingerprint purchase media, unlock your device, and log in to many apps and websites. Face ID on select iPhones and iPads takes security to a whole new level by using your face as a key.
5. Secure Enclave

If you're worried about scanning your face or finger, don't. It's not an image that's stored on your device, but rather a mathematical representation. Not only is it virtually impossible to reproduce the imagery, but it's kept on a chip Apple calls the Secure Enclave, which is separate from the rest of your device’s data and isn't stored online.
4. iCloud Keychain
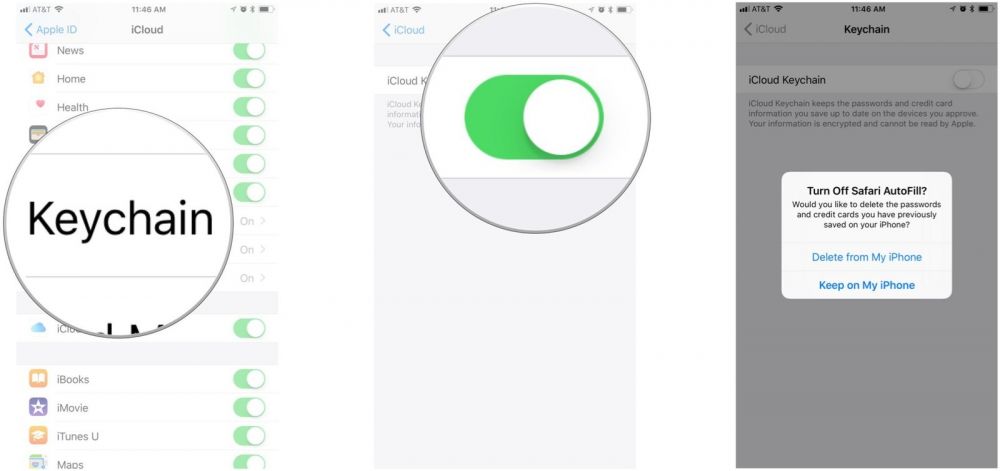
You can opt to save your passwords in iCloud with Keychain. This makes it easy to set strong passwords and forget about them. Speaking of strong passwords, Keychain can also suggest/generate strong passwords so you don't have to come up with them on your own.
3. VPNs
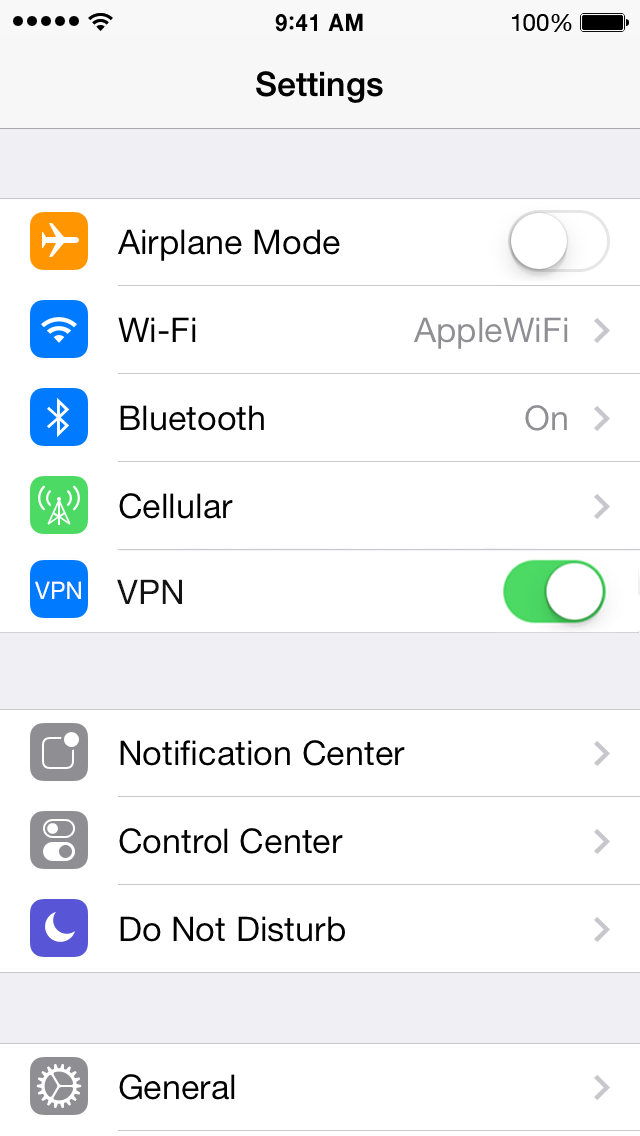
An added measure of security online is using a VPN—virtual private network. A VPN essentially hides your data from prying eyes by encrypting it end-to-end. Both macOS and iOS let users connect VPNs and many apps are available that allow you to configure a VPN quickly. 1.1.1.1 is a secure DNS server you can set, and it offers a VPN client for iOS.
2. Nothing Beats Common Sense

At the end of the day, education and common sense are your best defense against hackers. It's really up to you to keep your data safe. So don't stop here. Find other sources that help you learn how to stay safe online and secure your data.
1. Final Thoughts

Online security is important. So is keeping your physical devices secure. Sure, there are plenty of things I didn't cover, like cookie theft, DDOS attacks, man-in-the-middle attacks, rainbow lists, and more. But hopefully, this article was helpful and informative enough to help keep you safe.
Please consider spending some time learning more about cyber security to keep yourself safe and in the loops. Keeping up-to-date on cybersecurity is a great way to avoid popular scams and hacking techniques. We love to hear your thoughts. Feel free to use the comments section and social media to discuss greats ways for staying safe online. Thanks for reading!
