5 Things You Need to Know About Meltdown and Spectre

If you’ve been on the internet in the last few days, you’ve probably come across the terms “Meltdown” and “Spectre” in some alarming headlines. Both are hardware-level exploits that affect billions of computers — and could allow attackers to gain access to your sensitive information. But through the media frenzy in the wake of their discovery, it’s easy to get lost. Press the right arrow to learn 5 things you you need to know, and how to help protect your computers and data.
5 What are Spectre and Meltdown?

Put simply, Meltdown and Spectre are the names for two security vulnerabilities recently discovered within a vast range of computer hardware. Both exploits use similar core concepts by exploring the architecture built into basically all modern computing systems. It isn’t light reading, but secretary researchers have published two whitepapers on the exploits: available here, and here.
The two exploits are similar but separate. Meltdown is a vulnerability that, for the most part, only affects Intel processors — but is dangerous for users handling sensitive information unprotected systems.
Spectre, on the other hand, can affect basically any modern computer system. The latter vulnerability is both harder to exploit and harder to protect against, so it can be deployed via most web browsers.
4 What’s At Risk?

Spectre and Meltdown both take advantage of speculative execution mechanisms on a CPU. Put in other words, they’re hardware-based flaws and they exploit mechanisms and design decisions in computer hardware that were deliberate. Both exploits are extremely serious, and leave billions of devices at risk.
Meltdown, which affects Intel CPUs, could allow malicious programs to read kernel memory. That could allow attackers to access sensitive data like passwords, documents, photos and emails.
Spectre, which comprises two exploit techniques, breaks the isolation between different applications on a computer. While it’s a bit more difficult to pull off, Apple has said that it can be exploited via JavaScript in a web browser.
3 What Devices Do They Affect?

The Meltdown bug affects devices with Intel processors. Spectre is wide-ranging, and in theory, can be used as an exploit on basically any modern computer processor. But the risk doesn’t stop at Macs and PCs.
Apple has claimed that Meltdown can affect iOS and tvOS devices, too (though watchOS devices seem to be safe at this point).
If a computer uses a vulnerable processor and is running an unpatched version of an operating system, then it’s at risk. The threat can also affect cloud infrastructure and systems that use vulnerable processors and OS versions.
Safe to say, this bug affects millions of systems. Though, directly, either exploit won’t pose any more risk to users who practice safe computing than other serious viruses, Slate points out.
2 How Apple and Others Are Proceeding
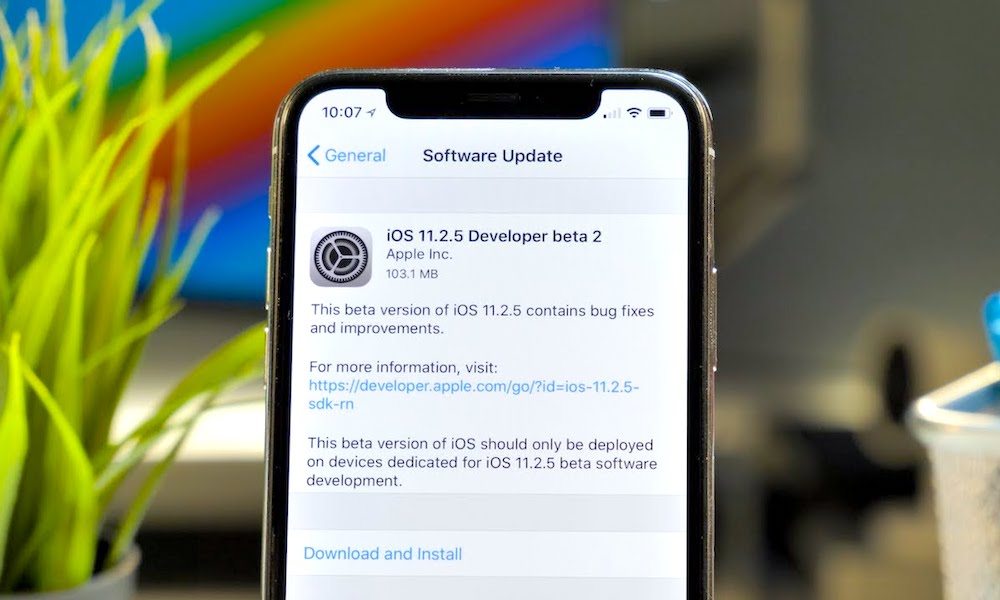
One of the primary issues with Spectre and Meltdown is that they exploit design decisions that were made to increase computer performance. Put simply, the way that we design computer processors allows for these exploits. And, in turn, attempting to fix the exploits could very well result in slower performance on a wide range of devices.
So while most major electronics makers — including Intel and Apple — are already issuing software updates and patches to mitigate the vulnerabilities, the implications could be wide-ranging. In fact, both exploits could change the way that companies design future processors and other computer hardware. For security researchers and tech companies alike, a great deal of work lies ahead.
1 What Do I Do?
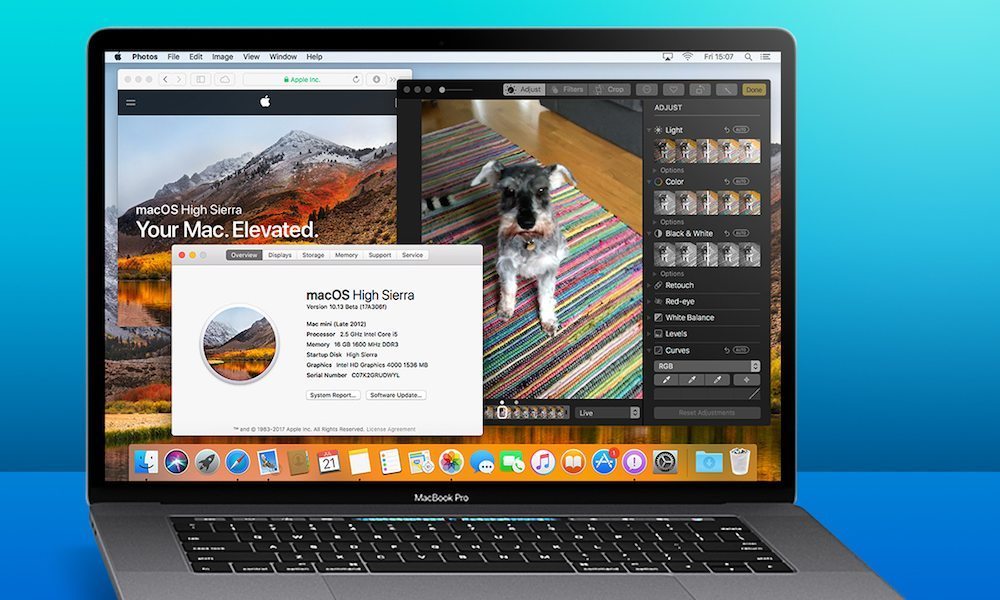
- First of all, the best advice is to find out if the operating systems you use are being updated with patches to mitigate the exploits. Most systems are — including upcoming Safari and Chrome patches that will be issued by Apple and Google which could reduce the risk of the Spectre exploit.
- Some government cybersecurity officials worry that the latest software patches aren’t enough, and that low-level firmware updates could be required.
- It’s also smart to practice safe computing strategies throughout all of your work on electronic devices — including the standard advice on avoiding computer viruses. Anti-virus software are already being updated to look out for viruses that use Meltdown and Exploit (so update them when you can).
- Additionally, refrain from saving any passwords in your browser or cache, and be cautious about the websites and services that you use.
